How To Copy Rfid Card With Phone
Radio Frequency Identification (RFID) is the wireless not-contact use of radiofrequency waves to transfer information.
Tagging items with RFID tags allows users to automatically and uniquely identify and rail inventory and assets.
More than ordinarily however RFID tags are used to access buildings such as gyms and apartment complexes.
Some of these can hands be copied and cloned so that yous can accept a spare one if yous need it.
RFID takes auto-ID engineering science to the adjacent level by assuasive tags to be read without a line of sight and, depending on the blazon of RFID, having a read range between a few centimeters to over 20+ meters.
How does the radio frequency identification Bill of fare work?
In several wireless smart cards, RFID applied science is existence used. Radiofrequency identification Smart Cards save details on a smart bill of fare flake. The bit features an integrated condom microcontroller and internal storage. Both the card and the reader interact through their integrated antennas using radio waves.
If the menu is placed into the reader'south electromagnetic field, the sensor in the card is activated. When the card is enabled, a wireless transmission interface is set up betwixt the card likewise as the data transmission reader. In the financial and banking market, Smart Cards have seen many uses non only for identity direction, security systems, storage, wellness, travel, mobile connectivity, etc.
RFID Fundamental Fobs
A key fob is a mechanical gadget that is tiny enough to connect to a keyring, which electronically opens or closes doors. The central fob has been the basis of the door admission locking organisation since it began in 1983. Early on devices, primarily used for auto doors, rely on line of sight while using infrared lights merely were highly susceptible to copying. Today, fundamental fobs operate by reliable, stable, and computerized RFID engineering science.
A fob-key RFID is a single element of an RFID device that has two principal components: a microchip, which stores the data, and an antenna for receiving and transmitting data. RFID key fobs are used in access controls such as apartments and hotel accommodation, authentication, mass transit, electronic payment, and much more than. Key fobs may exist cloned and hacked, hence it is vital that staff exist trained to safely utilise, store and bear them.
How do key fobs piece of work?
The RFID is the smart barcode engineering science that uses electromagnetic waves to allocate and trace information on "tags" that hold encrypted data. The data travels forth with radio signals. If yous desire to unlock the door with a key fob, just go along or wave your fob before the scanner.
Each pull a fast one on includes a single frequency microchip that interacts with the readers and shows that the door must exist unlocked. Fobs may be configured to enable admission levels for various applications.

How To Re-create RFID Key Fob Using The RFID Reader?
If you choose to clone a cardinal menu, go along the strips or chips with the encrypted details of the card confronting the RFID reader to scan it.
- Press the "Write" button on the reader while belongings it. At present click the bit on the rear of the RFID unit's newest switch, simply as you did the original. Pressing the "Edit" button would indent the source fob data on the new fob, which will serve as an accurate duplicate of the source.
- Instantly after duplication, evaluate the cloned key fob to ensure that it works. If not, make another try and get-go re-reading the source key.
- You tin can make duplicate copies of the original fob as much every bit you like while using the "Write" feature on several blank tags.
How to copy RFID cards (125khz) with an RFID copier?
The "Handheld RFID Writer" functions as follows:
- Switch on the screen and hang onto the maximal grip side of the compatible EM4100 card or fob and printing on the "read" control.
- If it works, the system will then make a noise, substitute the replicated tag with a blank tag and click "Write".
- The data contained in the source tag is then transferred to the new tag.
What is an NFC Card
Two computerized devices can communicate with 1 another past using near-field communication (also known as NFC). For eg, an NFC card and a card reader tin can interact with 1 another having a reading range of approximately 4 cm providing more than versatility than a contact card.
How to Clone an NFC card?
NFC cards have no-cloning security. These cards are meant as hands readable data containers. Anybody can translate NDEF from a menu and repeat it into another bill of fare. Mifare NFC 1K Cards tin exist very hands cloned with an Android handset having NFC functions. Yep, your smartphone could be used to jeopardize a house'south safety by using this kind of carte.
Only install Android's "Mifare Archetype Tool" and start making clones of cards that have never modified the default login credentials in the industry.
What are HID Cards
HID cards are products that use RFID communication technologies and are too known every bit prox cards, proximity cards, and access control cards. HID is one of the major suppliers of smart prox cards and provides a standard for prox admission control devices.
They are piece of cake to work with and compliant with all scanners of HID proximity cards. PVC HID cards can be easily printed and designed. HID identification cards are widely used in offices, workplaces, educational institutions for admission control.
Can y'all Copy HID cards?
HID smart cards are best suited for applications where a stronger degree of protection is needed. Smart cards similar the iCLASS production range of HID Global are almost impossible to replicate when accordingly handled. Any HID carte cannot be cloned.
There are various formats of cards and different and specialized strategies might be required based on the blazon. The differences lay in the depth of encryption.
How to Defend against Card cloning
RFID is among the most popular encryption solutions and is also one of the simplest and easiest to clone. If you presume these cards are 'secure,' 'safe,' or 'impossible to scissure,' information technology's incorrect.
Because currently in that location are several different forms of card technologies, and "proximity cards" are the virtually insecure card types. So if anyone tries to clone an RFID card, it isn't very difficult.
RFID Blocking Wallet
The merely fashion to safeguard yourself confronting RFID cloning is to utilise an RFID-blocking wallet or cover. This works simply by suppressing the RFID's indicate. When there isn't a signal interloper, the specific data on the device cannot be collected and it cannot be copied.
The drawback of this solution is how this is applied to a collective of workers with access cards. It should be a prerequisite for workers to utilise RFID wallets or covers to keep their cards secure.
Two-Factor Authentication
RFID cards can be easily copied. To secure these cards from cloning and unauthorized access we tin use the 2nd form of verification. This process is known as 2-cistron authentication.
Often access direction systems pair a security carte with a security question whose respond is but known to y'all." In this process, you set up a security question and y'all are the but i with its answer. Another way to secure your card is by using your smartphone 2 to receive a lawmaking earlier admission control.
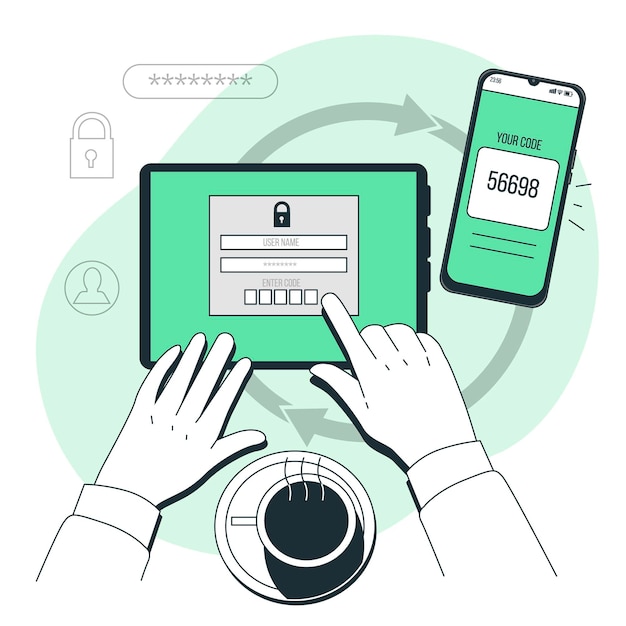
Mobile Pass Solution
Admission Command visitor Brivo provides the Brivo Mobile Pass solution. This arroyo completely removes the need for actual RFID security cards and scanners. The Mobile Laissez passer solution uses a mobile app to give access to secure doors.
Contactless Smart Carte Technology
In contrast to 125 kHz, smart cards use 13.56-MHz. Its embedded systems can collect, process, and oftentimes interact through radio waves with a concluding. The correspondence between both the carte and the reader, dissimilar proximity cards, is protected and secure. In this solution of security card systems, nosotros use the incredible technology of SEOS. These cards are also suitable for information sharing and are platonic for logical access command.

Frequently Asked Questions
Here are
Conclusion
The majority of companies around the earth have security mechanisms in place and use RFID security key cards to decide who has access to sensitive parts of the company's facilities. However, these devices can exist easily cloned, even from a distance of several yards, without anybody realizing their protection has been violated.
There are security features that tin help reduce the risk of employing RFID technology to manage physical access. The most straightforward method is to utilize a gimmicky RFID system with encryption capabilities. In order to give access to some highly restricted places, a genuinely comprehensive concrete security system relies on numerous types of identification.
If your company already has dubious RFID privacy and is unable to modernize its infrastructures, there are still some simple procedures that may exist taken to foreclose RFID carte du jour cloning. RFID blocking wallets, for example, will prevent your cards from existence copied by blocking whatever unwanted RFID signals.
How To Copy Rfid Card With Phone,
Source: https://rfidprivacy.us/how-to-copy-an-rfid-card/
Posted by: kuhnamin1981.blogspot.com


0 Response to "How To Copy Rfid Card With Phone"
Post a Comment